In today’s fast-paced business environment, success is driven by the productivity and efficiency of your workforce. CoAction's Continuous Workforce delivery model simplifies...
Preparing for the Worst: Enhancing Cyber Resilience with CoAction’s Tabletop Exercises (TTX)
When it comes to cybersecurity, preparation is everything. While no organization can fully eliminate the risk of a cyberattack, how you respond during a crisis makes all the...
A Roadmap to Enhanced Security: Implementing Zero Trust with CoAction
Zero Trust: The Foundation for Secure Business Enablement The cybersecurity landscape is evolving rapidly, with businesses facing persistent and sophisticated threats....
Zero Trust Exchange: The Future of Secure and Efficient Networking
Zero Trust: The Foundation for Secure Business Enablement The cybersecurity landscape is evolving rapidly, with businesses facing persistent and sophisticated threats....
Zero Trust: The Foundation for Secure Business Enablement
Introduction The cybersecurity landscape is evolving faster than ever, with organizations facing increasingly sophisticated and persistent threats. Traditional perimeter-based...
Defend Your Small Business: CoAction’s SMB Fraud Defense Solutions
Introduction Cybersecurity threats are evolving rapidly, becoming more sophisticated and pervasive each year. For small to mid-sized businesses (SMBs), these challenges are...
Frontline Cyberwarriors: Comprehensive Cybersecurity Services by CoAction
Introduction In today’s rapidly evolving digital landscape, businesses face an ever-growing array of cyber threats. From data breaches to ransomware attacks, these challenges...
Empowering Data Management Together: CoAction’s Partnership with Congruity360
Empowering Data Management Together: CoAction's Partnership with Congruity360 In the evolving landscape of data management and compliance, staying ahead means leveraging...
Enhancing Awareness of Identity-Based Cyber Threats with CoAction
Enhancing Awareness of Identity-Based Cyber Threats with CoAction It is alarming to learn that 80% of security breaches involve compromised identities, often taking as long as...
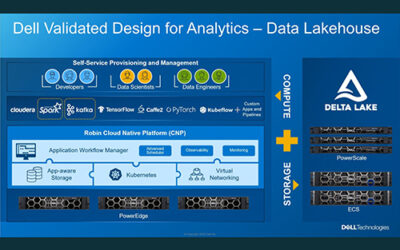
Revolutionizing Data Management with Dell Data Lakehouse
In an era where data complexity challenges continue to escalate, the unveiling of the Dell Data Lakehouse presents a groundbreaking solution aimed at streamlining data management...
Cybersecurity Strategies for Small Business Growth
Cybersecurity Strategies for Small Business Growth For small business owners, growth is the north star. In pursuit of this, they often find themselves juggling roles from sales,...
Network Denial of Service (DoS) attacks: Understand, Mitigate and Solve with CoAction
In the field of cybersecurity, Network Denial of Service (DoS) attacks present a notable and increasing issue for organizations operating online. This article aims to clarify the...
Ready To Contact Us?
Reach out today and see how, CoAction can help you.